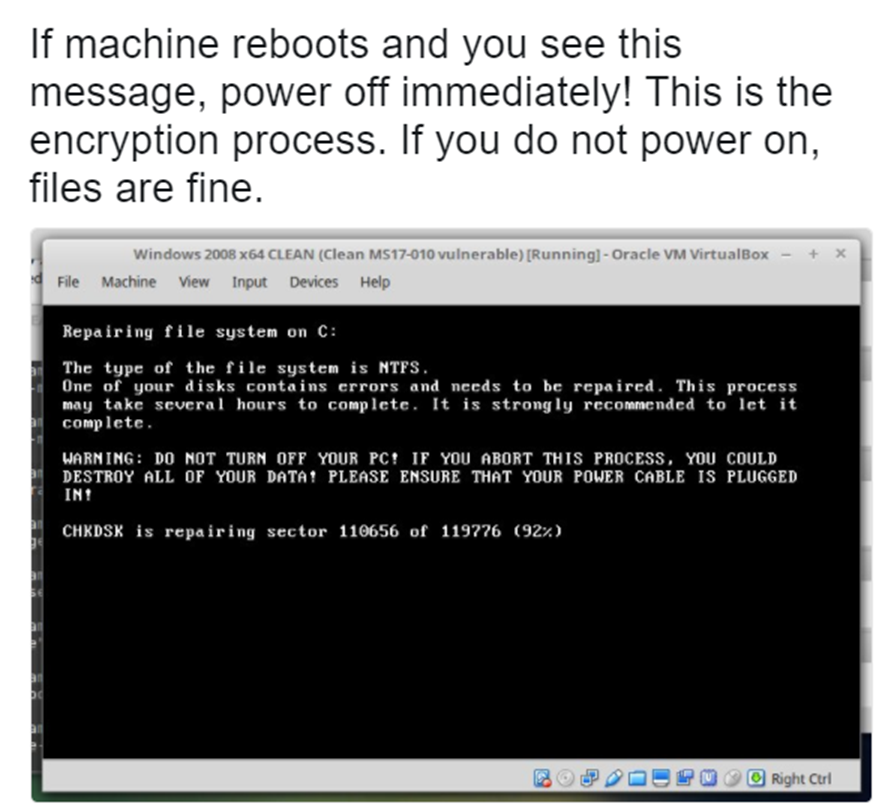
Another Cyrptovirus has reared it's ugly head in the wild called Petya. It's already infected an Ukrainian Bank , DLA Pipa Law Firm in the USA and a few other agencies.
So far there has been no kill switch found to stop mass infection.
It utilises the same flaws that Wanna Cry used with SMB 1 so if you have already disabled this you should be some what protected. This virus gets into organisations through Email to Spam Filters behind your email servers are a real time defense against these new virus as well as up to date Windows and anti Virus on your Firewall.