As we approach the holidays, Response IT wants to update you on our availability during the festive period. Read our latest blog post for business hours during Christmas and New Year.
Important notification: service change freeze during festive period
Apple releases updates to fix security flaws
Response IT launches ServiceNow to enhance IT support capabilities
Log4shell Vulnerability: Advisory Notice
Modern Networks joins forces with Response IT
Modern Networks joins forces with Response IT to support regional growth, increase resources and enhance customer service.
Response IT is pleased to announce that the company has joined forces with Modern Networks. The investment is part of Modern Networks long term strategy to double the size of its business following a major investment by Horizon Capital in April 2021.
Better together
Uniting Response IT and Modern Networks will create a stronger and more competitive company. The investment supports Modern Networks regional growth plans and increases resources, which will enhance all aspects of customer service.
Greater support
The combined Modern Networks/Response IT business will now operate on a larger scale, serving over 6,000 users, 1,800 commercial properties, 300 medium sized businesses and not-for-profit organisations across the UK. Our customers will be supported by our growing team of 150 employees working from four sites in Hitchin, Cambridge, Manchester and Guildford. Additionally, we have five engineers permanently based in central London, to provide fast local on-site support.
Nothing changes for now
Initially, Response IT and Modern Networks will continue to trade under their existing brand names however in time Response IT will be integrated into Modern Networks. Response IT customers can rest assured that we remain committed to customer service and support and this union will enable us to offer broader services to all our customers. Naturally, we will be writing to each and every customer with more detailed information.
Committed to our customers
Response IT and Modern Networks have a track record of working closely and developing in-depth, long-term customer relationships. As a united business we remain committed to our customers and providing innovative IT, telecommunications and broadband services that meet your specific needs.
To learn more about Modern Networks acquisition of Response IT, please visit www.modern-networks.co.uk/news
Thank you
What is EPP ( Endpoint Protection Platform ) ?
An endpoint protection platform (EPP) is a solution deployed on endpoint devices to prevent file-based malware attacks, detect malicious activity, and provide the investigation and remediation capabilities needed to respond to dynamic security incidents and alerts.
Methods of Endpoint Protection Platform would be
Prevent File-Based Malware like normal Antivirus
Detect and block Malicious activities from trusted and untrusted applications
Provide the investigation and remediation capabilities to respond to security incidents and alerts
Integrate machine learning to support to give it intelligence to identify behavioral analysis ( what a normal program and malicious code would usually do )
What’s the difference between Antivirus and Endpoint Protection Platform?
Traditional antivirus use a hash ( Signature ) of a file which its pre-determined to be malicious in a database and deletes this file and stops it from running.
It does have some intelligence using Heuristic analysis to analyze source code ( code of software ) and comparing its behavior to a database of known threats
It is also available to check for programs corrupting Operating system files which is how machines are infected.
Due to Polymorphism (which is a virus being able to mutate itself on demand every time it runs ) normal Antivirus cannot detect these constantly changing variants. This is why Traditional AntiVirus’ are getting fazed out and being replaced by EPP or EDR solutions which intelligence behind them to detect these new constantly evolving threats.
If you are a customer of ours you would probably have Webroot which has EPP capabilities built-in :
What is EDR\ETDR- Endpoint ( Threat ) Detection and Response?
This term was invented by Anton Chuvakin from Gartner to categorize
tools primarily focused on detecting and investigating suspicious activities (and traces of such) other problems on hosts/endpoints
Typical Activities of an EDR System
Record and store endpoint behaviors and events
Detect Security Incidents
Response forensics ( Investigate Security Incidents with Root Cause Analysis )
Response Containment and diagnosis
Gartner Provides a List of Current EDR Providers
What is the difference between EDR and Antivirus?
A traditional antivirus will clear a system\organisation of the threat, but EDR software goes into investigation mode. Based on its sequence of recorded events, it presents how the attack played out on your company's computers, noting every change to the system. This playback of the event often looks like a branching flowchart that starts with the initial incursion and proceeds to describe which parts of the system and network were infected, when, and what the result was. E.g. one from Crowdstrike below
EDR can help stop attacks like at traditional antivirus, the software still needs an effective backup policy to restore key data to infected systems.
EDR also protects employees away from malicious websites with a history of virus and malware. It enables the categorization of websites to webfilters to stop pornography, advertising sites, gambling and gaming sites because these are usually highways for malicious files and added extra protection to stop phishing attempts. It also enables you to protect your workforce while they are away from the office and not protected by the companies firewall
EDR Pricing
EDR Solutions are way just more than traditional files scanners , if you don't have IT staff, you'll likely want to outsource the monitoring of the EDR dashboard. Per endoint , prices can vary from 10GBP to 30GBP per seat per year
Password Manager coming to Office 365 Soon!
Last December, Microsoft announced updates to its Microsoft Authenticator app
If you haven’t heard of this app before, it is the default two-factor authentication that should be for any Office 365 tenants 2fa prompts due to Sim Hijacking.
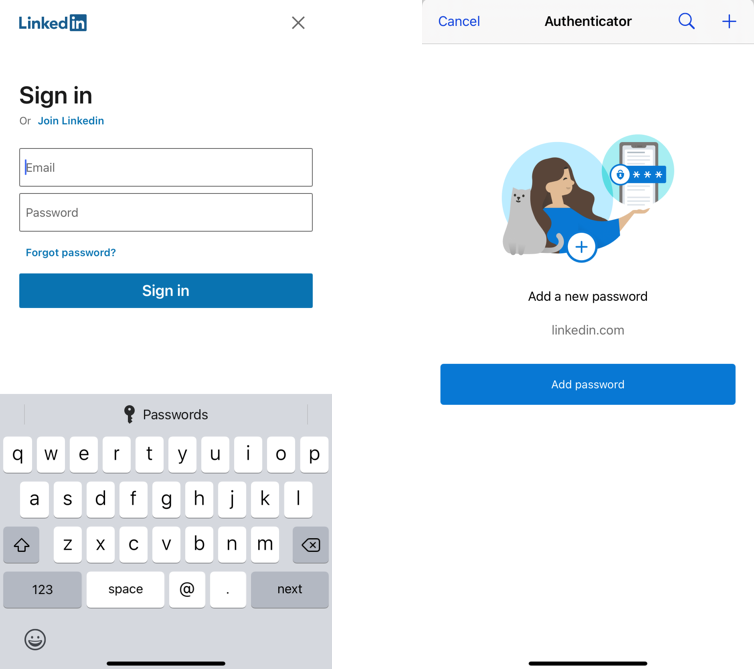
The App update included the ability to store Website Passwords using Autofill , however as its in preview only if you have a Personal Microsoft Account registered to the device. Microsoft has not made this available to 365 users as of yet , probably because its in preview , until they iron out the bugs! They are allowing some organizations to be on this beta list. Click here to try yourself
When you visit a site or app for which you have saved a password, Authenticator offers to autofill it.
Two useful Reports Built Into Windows 10 to help identify computer issues
netsh wlan show wlanreport
The wireless network report is one of the more useful tools in Windows 10 that can help you diagnose Wi-Fi connection problems.
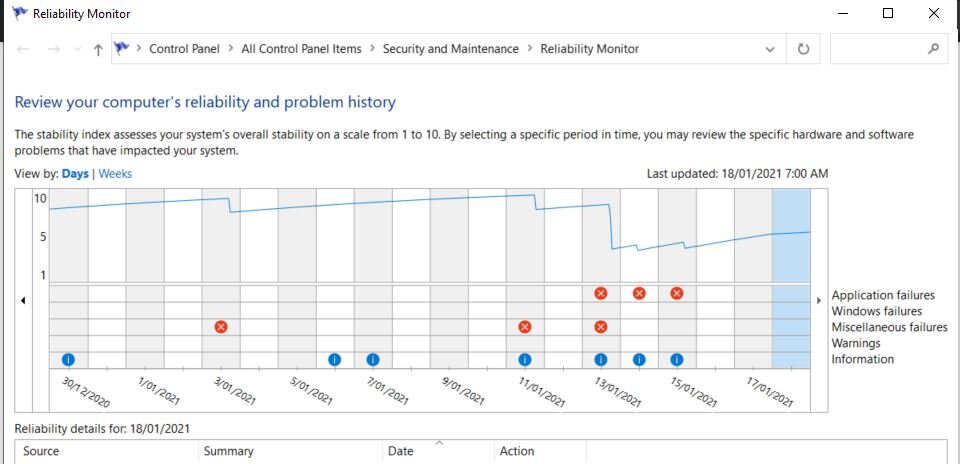
Reliability Monitor
Windows Reliability Monitor is a feature found to view the stability and issues with your computer. Produces a graph for you to identify previous warnings and past critical and informational events from the event log. Each day is different columns. When a column is clicked, additional details appear about that particular date.
Azure AD - Continuous access evaluation ( CAE )
Continuous access evaluation ( CAE ) is a new version ( Currently writing this still in Preview ) of identity security from Microsoft Azure AD which involves the terminating of active sessions to Office 365 services such as Exchange, Teams and Sharepoint in real-time instead of waiting for a Token Expiry.
Currently when you perform tasks such as :
Reset a Users password
Disable their Account
Enable them for MFA
You need to wait for their session token to expire, so the user is removed from accessing services. The token length duration can be reduced from the default of 1 hour to 10 minutes , however this still gives an ex gruntled employer, for example, 1a minimum 10 minutes to email Customer or Employers after termination.
The manual method to force the refresh is to log out session in the 365 portal below
How with Continuous access evaluation ( CAE ) this is no longer needed!
Applications that support Continuous access evaluation ( CAE )
Outlook for Windows, iOS, Android, Mac and Web App;
Teams for Windows, iOS, Android and Mac (Only for Teams resource);
Word/Excel/PowerPoint for Windows, iOS, Android and Mac.
What is the cost?
At least one Azure AD Premium P1 license is required in your organization
Policy’s and Procedures Company’s should have on file
Acceptable Use Policy
Rules for the acceptable use of information and assets associated with information processing facilities.
Additionally covering internet access policy, BYOD policies as part of this.
Antivirus Policy
Detection, prevention and recovery controls to protect against viruses.
Information Classification and Data Policy
Information classification in terms of its value, legal
requirements, sensitivity and criticality to the organization.
Additionally covering Disposal of Information Policy +Data Classification Guidelines/procedure as part of this (procedures for information labelling and
handling). Additionally covers destruction of data on removable media. CPS 234 guidelines are also covered as part of this.
Clear Desk and Clear Screen Policy
A clear desk policy for papers and removable storage media and a clear screen policy for information processing facilities.
Email Policy
Appropriate protection of Information involved in electronic messaging.
IT Mobile Computing Policy
a. The process that mobile computers must meet to leave the company network.
b. How mobile computers and devices will be protected while outside the organizational network.
c. The process that mobile computers must meet to enter the company network when being brought into a building owned by the organization
Password Policy
Guidelines for managing passwords.
Physical Security Policy
Physical security for offices, rooms, and facilities by appropriate entry controls, Physical protection against damage from fire, flood, earthquake, explosion, civil unrest, and other forms of natural or man-made disasters.
Risk Assessment and Handling Policy
Overall process of risk analysis and risk evaluation. Operating controls to manage an organization's information security risks in the context of the organization’s overall business risks
Change Management Policy
Policy to manage changes to organisation, business processes, information processing facilities and systems that affect information security.11
Remote Access Policy
Policy for teleworking activities, VPN and remote access of organisation resources.
Covering VPN policy as part of this
Security Incident Management Policy
Policy to raise, handle and resolve information security incidents.
Wireless Communication Policy
Specifies the conditions that wireless infrastructure devices must satisfy to connect to the Wireless infrastructure of the organisation. Only devices that meet the standards specified in this policy are allowed to connect to corporate Wifi infra.
Patch Management Procedure
Provide the guidelines for the use and deployment of the Patch Management Solution within the organisation
Vulnerability Management Policy
Information about technical vulnerabilities of information
systems being used shall be obtained, the organization's exposure to such vulnerabilities evaluated, and appropriate measures taken to address the associated risk.
Business Continuity Planning Procedure
This is a detailed plan developed to enable continuity of operations of the organisation in an event of a disaster. The provisions of this plan will be used as the basis for guiding recovery activities, DR (disaster recovery) aimed at operating Core business functions at a pre-determined minimum acceptable level of service.
Application Development and code review procedure
Set of security guidelines to be followed at the time of software development and to establish a code review mechanism
Audit Log and Monitoring Policy
Deals with handling and storing system critical logs and their ongoing monitoring.
Access Control Policy
The policy specifies how to manage access control to organisation's critical assets and provide appropriate access controls to protect information processed/ stored in computer systems. To prevent unauthorized access to data or system resources.
Key Management and Data Encryption Policy
Use of cryptographic controls for protection of
information .Key management process to support the organization’s use of cryptographic techniques.
Information Security Policy
This policy document provides the framework to develop and disseminate an information security policy in order to achieve organisation security objectives. This policy document is the master document, which is supported by other documents governing Information Security Management System compliance within the organisation
Third Party Provider Policy
This Policy outline the requirements for engaging, monitoring and working with vendors, External Service Provider (ESP), service provider partners and contractors.
Mandatory Data Breach Notification Policy
This policy sets out procedures for managing a data breach, including the considerations around notifying persons whose privacy may be affected by the breach.
Microsoft Power Apps: Business Apps from the ‘Microsoft ‘Power Platform’
PowerApps is a part of the ‘Microsoft ‘Power Platform’ built into Office 365 suite which is used by organizations to develop internal tools for the Web and mobile devices with little developer experience ( think of it as a combination of PowerPoint and Excel )
The interface is very user friendly allowing you to drag and drop text/icons/pictures into each screen of the app , the data manipulation can be performed by excel-like queries.
Power apps has three main features
Powerapps can get its data from a range of existing apps or create new datasets from scratch. To give you an idea of what this can be used for you can see demo’s below of tools that are usually done by hand or excel sheets.
Another big plus for Powerapps is you can integrate the Powerapp into Teams which should already be deployed across your organization which makes App rollout fast and painless.
Cost
Running a single app is 7.50GBP / Person / Month
Running Unlimited Apps is 30.20 GBP / Person / Month
Risk Assessment Questionnaire for your Company
A risk management framework (RMF) is the structured process used to identify potential threats to an organization. If you deal with Government data you usually enter into an agreement that you comply with one these frameworks.
A standard framework in the industry is NIST Framework
This involves detailing all parts of your company in a questionnaire such as the below
https://watkinsconsulting.com/our-projects/nist-csf-excel-workbook/
After this, you will have a list of risks ( Risk Register ) and the Maturity levels for each Function
If you do not need to currently comply with a Framework, we recommend self-evaluating your company with the below simple tool
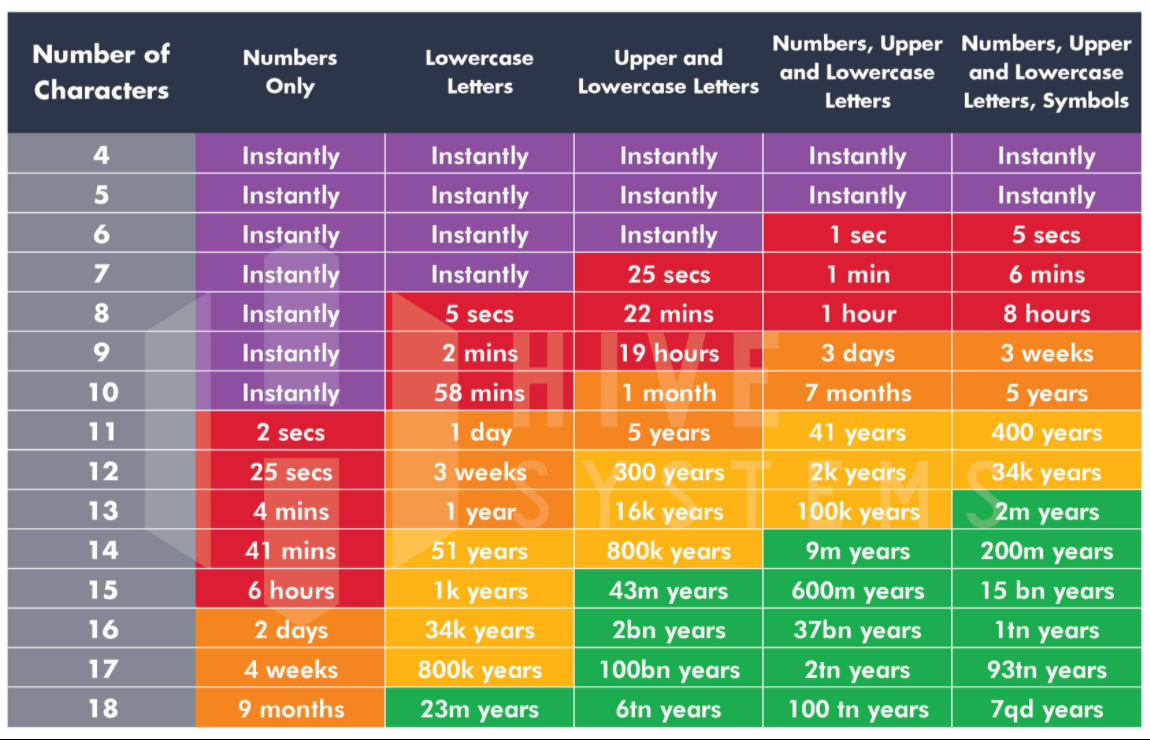
How long does it take to crack your password?
These numbers as the time it takes if a Hask of your password was obtained and then bruteforced. This can be achieved using latest hardware that can be readily purchased on the market,Gigabyte GeForce RTX 2080 Ti Turbo 11GB Graphics Card with Costs about 1000 GBP
What do I do?
You can see in the graph that you will need a minimum 10 Characters length password with differing UpperCase\LowerCase\Symbols and Numbers to hold up to a brute force attack.
It is recommended now to use Password Phrases instead of a single word for example
door cisco 2452 tree!
365 Attack Simulator in ATP vs Knowbe4 for Phish training
We have talked before about companies running internal Spear Phishing Tests internally to check if any users need training of how to spot potential attack vectors
There are a wide range of platforms to choose from
Mimecast recently purchased a company to add it to their service offerings
Office 365 has added Phish Simulation to their Offerings in ATP Plan 2 so we thought we would compare it to the current industry leading ( according to Gartner ) solution Knowbe4 per below
| Office 365 Attack Simulator in ATP | Knowbe4 Diamond Package | |
|---|---|---|
| Cost | 3.80GBP/User/Month | 2GBP/User/Month |
| Licensing | Per User | Whole Organisation |
| Password attack campaigns | Yes | No |
| On Prem and 365 Mailboxes | Yes | Yes |
| USB Drive Test | No | Yes |
| Video Training Access | No | Yes |
| Phishing Reply Tracking | No | Yes |
| Templates available | 2 | 100+ |
| Vishing Security Test | No | Yes |
| Whitelisting Required | No | Yes |
| Users Sync Needed | No | Yes |
Knowbe4 has a must more customisable solution for enterprises with API intergration and larger offering , however for Small Business’ wanting to add to ATP Plan 1 , the Attack Simulator ticks that box for compliance in regards to running Phish Simulations.
Microsoft Azure - Windows Virtual Desktop \ Desktop-as-a-Service
Windows Virtual Desktop uses Microsoft Azure to provide the infrastrucutre services ( Broker\Monitoring\Diagnostics\Web Access\Gateway) needed to host a Windows 10 Enterprise multi-session Operating System – which is completely optimized for the sake of Office 365 ProPlus services, such as Outlook, OneDrive Files on Demand (per-machine), Teams etc and supports the addition of High End GPU’s for Graphics Processing
In terms of labour needed for the IT management of the system , the only effort is the Machine images on top of Azure Infrastructure-As-a-Service (IaaS). The rest is all managed for you through the Azure service SLAs
Licenses Needed
To run Windows 10 multi-session ( You will need Office 365 Shared Activation to run O365 )
Microsoft 365 F1, E3, E5, A3, A5, Business
Windows 10 Enterprise E3, E5
Windows 10 Education A3, A5
Windows 10 VDA per user
To run Windows Server 2012 R2, 2016, 2019
Remote Desktop Services (RDS) Client Access License (CAL) with active Software Assurance (SA)
Profiles
FSLogix Profile Container can be leverage with Azure Files to Store users Settings. Most of their documents should be stored in Onedrive to keep costs down
Authentication
Existing Azure AD Tied with Office 365 can be leveraged for access \ security and permissions ( Conditional Access )
Network
Microsoft Provides a Tool you can check your current internet connection Latency to Azure
Costs
Using the Azure Calculator ( which has a minimum seat count of 100 ) you can get a rough cost of users e.g. for Medium workload and 1TB space = 900GBP/Month
You just need to then virtualise you OnPremise Apps and Servers to Azure and you have just gone full cloud
Data Loss Prevention Polices Business' should have for ISO 27001 certification
Obtaining an ISO Certification means companies need to have Polices written to and abided for in regards to Data Access and Prevention of Data Loss
Information Classification, Labelling and Handling
Development of a policy that defines the data companies own and use (both in motion and at rest) and guidelines on effective and secure handling and communication of said data.
Data Access Management
Development of a data access management policy to ensure that users only gain access to the data they need to perform their work function.
User additions, changes & removal
Policy & associated process to ensure starters and leavers are processed properly and all security considerations are taken care of.
Report to show access by user. Regular reviews of access and passwords.
Report to be delivered on a quarterly basis to Mark for review with the business.
Reponse IT work with business to make sure their technology stack can Audit and report on all of these as well as helping you write your internal IT Policy
Should you Backup your Office 365 Infrastructure?
Office 365 has lots of redundancy built into their network , which covers you automatically from Hardware, Software, or Corruption, so you are somewhat automatically protected from failure.
Some companies don’t trust what they can’t see with the cloud so they like locally hosting their data.
Office 365 Retention Policies
You can add a “Forever” retention policy to your Office 365 tenant which means items can never be deleted for free. Officially this is part of the Office 365 Enterprise License ( E1-E5) However even on the Business Essential / Premium Products you can still enable this and lookup deleted emails.
Why Backup is different from Retention
Say for example you have a retention policy enabled. A user re-arranges a load of emails from one folder to another folder and so on , then down the line wants to revert all her changes. You cannot use the retention policy to restore these as they have never been deleted. This is where you need a backup of the previous day or hour when you have a snapshot of that folder to restore too.
Veam
If you are backing up Virtual machines you probably will be using Veeam to an offsite and onsite location.
Veeam offers a free Veeam Community Edition for 10 Users or Less ( No Support ) which will integrate into your existing infrastructure
Synology NAS
If you still have on-premise servers you are probably using an Onsite NAS to back these up to.
If you are using a Synology NAS , any 64-bit NAS with DSM6.1 or later with 2GB of RAM or more, supports “Active Backup for Office 365” package on Synology. This allows to backup drive, mail, contacts and calendar… items. For Free!
https://www.youtube.com/watch?v=pBK0pI7qF6A&feature=youtu.be
supported models: https://www.synology.com/en-us/dsm/packages/ActiveBackup-Office365
Just because you have a backup it is not saying there won’t be any downtime to your company if a service goes down or an error occurs that needs to be restored from. Backups usually have a Restore time of 4-24 hours depending how much data needs to be restored.
If you are looking for a Zero Company downtime solution you will want a service such as Mimecast Continuity
Windows 10 - Shared VS Kiosk Machine
Windows 10 Kiosk Mode
Windows 10, version 1703, introduces a mode called “kiosk mode”. What happens in Kiosk mode is Windows Signs in Automatically to a restricted local user account ( in case of a computer restart ) and runs in either a single Microsoft Store app full-screen mode inside (above the Lock screen) that prevents anyone from accessing the desktop, switch apps, or change settings, or it can run in multi-app kiosk mode ( Windows 10, version 1803) where only a certain number of apps can be run.
What would this be used for
Digital Signage - Small Intel NUC devices outputting a single webpage with company/school updates to a screen in a shared area
Kiosks inside of a Retail environment - Such as a Point of Sale device logging into Point of sale app e.g. Sassco Point of Sale
Computers providing internet access to Guests in Airports / Hotels or Events
Kiosk mode is not available on Windows 10 Home.
Windows 10 Shared Mode
Windows 10, Verison 1607, introduced Shared PC Mode
Windows 10 Shared PC Mode deletes old guest accounts automatically, because every time a guest logs in, it creates a new profile, which takes up disk space. This is useful for computers which have different people logging into the device every day and stops excess profiles building up using storage
What would this be used for?
University Computers
Internet Cafes
Both of these modes can be set up and managed through a domain controller or GPO or even better a cloud managed solution such as intune which means devices can be rolled out to different locaitons and all they need is an internet connection










![Microsoft-power-platform[1].png](https://images.squarespace-cdn.com/content/v1/5e3af6fc8b0fb76851c5cb4f/1601855216869-Z44U3NRLKMRG4RJ7P2VX/Microsoft-power-platform%5B1%5D.png)
![NIST_CSF[1].jpg](https://images.squarespace-cdn.com/content/v1/5e3af6fc8b0fb76851c5cb4f/1599887376477-0KDKE0GEOVYOQ90V109G/NIST_CSF%5B1%5D.jpg)