According to the UK Government, in 2014, 60%* of SMBs experienced a security breach. The same survey has estimated that a severe cyber attack on a SMB costs upwards of £65k.
*UK Gov, The Information Security Breaches Survey – Department of Business, Innovation & Skills
Since 2014 Security risks and attacks have increased in quantity and sophistication
The government has put together some free training for companies to train staff of how to protect security
https://www.gov.uk/government/collections/cyber-security-training-for-business
What do you get from a Security Assessment?
We look at your current system as it currently is to locate and identify an potential security vulnerabilities and risks. It's a great way to get a third party audit of your current network and system and also a list of recommended upgrades or changes in a single report.
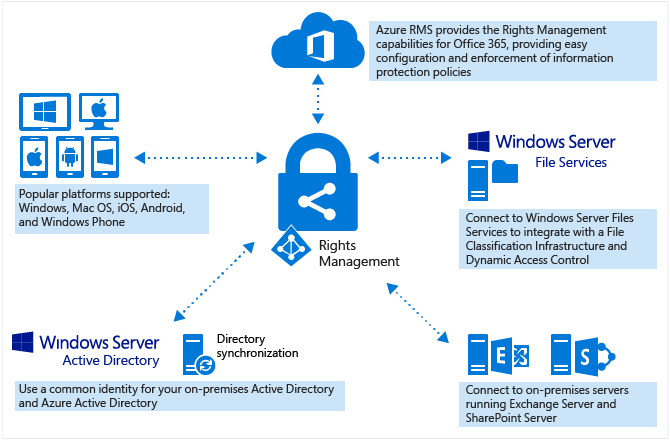
Access Control - Who currently has access, do they need access, how they access and what to
Patch Management - What is up-to-date and what isn't in your company with list of security exploits that can currently be used against your system
Malware Protection - What current defense do you have against virus, spyware and spam
Firewalls - Your current firewall configuration
Backups - Your current backup configuration
Why should I get a security assessment?
A security assessment can prove beneficial to companies to not only reduce the risk for future attacks, but it can also offer up significant financial advantages. One of these advantages is the review of your current spending of the above to check for any unnecessary overspending on certain security solutions and suggest the most cost efficient alternatives available
Contact Response IT Today via our Contact Us Page to Inquire about our IT Security Assessment